- To adjust to a brand new EU legislation, the Digital Markets Act (DMA), which comes into drive on March seventh, we’ve made main adjustments to WhatsApp and Messenger to allow interoperability with third-party messaging providers.
- We’re sharing how we enabled third-party interoperability (interop) whereas sustaining end-to-end encryption (E2EE) and different privateness ensures in our providers so far as potential.
On March seventh, a brand new EU legislation, the Digital Markets Act (DMA), comes into drive. Considered one of its necessities is that designated messaging providers should let third-party messaging providers develop into interoperable, supplied the third-party meets a collection of eligibility, together with technical and safety necessities.
This permits customers of third-party suppliers who select to allow interoperability (interop) to ship and obtain messages with opted-in customers of both Messenger or WhatsApp – each designated by the European Fee (EC) as being required to independently present interoperability to third-party messaging providers.
For practically two years our staff has been working with the EC to implement interop in a manner that meets the necessities of the legislation and maximizes the safety, privateness and security of customers. Interoperability is a technical problem – even when targeted on the fundamental functionalities as required by the DMA. In yr one, the requirement is for 1:1 textual content messaging between particular person customers and the sharing of photographs, voice messages, movies, and different connected recordsdata between particular person finish customers. Sooner or later, necessities increase to group performance and calling.
To interoperate, third-party suppliers will signal an settlement with Messenger and/or WhatsApp and we’ll work collectively to allow interoperability. In the present day we’ll publish the WhatsApp Reference Supply for third-party suppliers which is able to define what can be required to interoperate with the service. The Reference Supply for Messenger will observe in the end.
Whereas Meta should be able to allow interoperability with different providers inside three months of receiving a request, it could take longer earlier than the performance is prepared for public use. We needed to take this chance to set out the technical infrastructure and considering that sits behind our interop resolution.
A privacy-centric strategy to constructing interoperable messaging providers
Our strategy to compliance with the DMA is centered round preserving privateness and safety for customers so far as is feasible. The DMA fairly rightly makes it a authorized requirement that we must always not weaken safety supplied to Meta’s personal customers.
The strategy we’ve got taken when it comes to implementing interoperability is the easiest way of assembly DMA necessities, while additionally making a viable strategy for the third-party suppliers interested by changing into interoperable with Meta and maximizing person safety and privateness.
Implementing an end-to-end encrypted protocol
First, we have to shield the underlying safety that retains communication on Meta E2EE messaging apps safe: the encryption protocol. WhatsApp and Messenger each use the tried and examined Sign Protocol as a foundational piece for his or her encryption.
Messenger continues to be rolling out E2EE by default for private communication, however on WhatsApp, this default has been the case since 2016. In each instances, we’re utilizing the Sign Protocol as the inspiration for these E2EE communications, because it represents the present gold customary for E2EE chats.
As a way to maximize person safety, we would like third-party suppliers to make use of the Sign Protocol. Since this has to work for everybody nevertheless, we are going to enable third-party suppliers to make use of a appropriate protocol if they’re able to show it affords the identical safety ensures as Sign.
To ship messages, the third-party suppliers must assemble message protobuf constructions that are then encrypted utilizing the Sign Protocol after which packaged into message stanzas in eXtensible Markup Language (XML).
Meta servers push messages to linked purchasers over a persistent connection. Third-party servers are liable for internet hosting any media recordsdata their consumer purposes ship to Meta purchasers (resembling picture or video recordsdata). After receiving a media message, Meta purchasers will subsequently obtain the encrypted media from the third-party messaging servers utilizing a Meta proxy service.
It’s necessary to notice that the E2EE promise Meta gives to customers of our messaging providers requires us to regulate each the sending and receiving purchasers. This permits us to make sure that solely the sender and the supposed recipient(s) can see what has been despatched, and that nobody can hearken to your dialog with out each events realizing.
Whereas we’ve got constructed a safe resolution for interop that makes use of the Sign Protocol encryption to guard messages in transit, with out possession of each purchasers (endpoints) we can’t assure what a third-party supplier does with despatched or obtained messages, and we due to this fact can’t make the identical promise.
Our technical resolution builds on Meta’s current consumer / server structure
We predict the easiest way to ship interoperability is thru an answer which builds on Meta’s current consumer / server structure [Figure 1]. Particularly, the requirement that purchasers hook up with Meta infrastructure has the next advantages, it:
- Permits Meta to maximise the extent of safety and security for all customers by finishing up lots of the similar integrity checks because it does for current Meta customers
- Constitutes a “plug-and-play” mannequin for third-party suppliers, reducing the boundaries for potential new entrants and prices for third-party suppliers
- Helps maximize safety of person privateness by limiting the publicity of their private information to Meta servers solely
- Improves general reliability of the interoperable service because it advantages from Meta’s infrastructure, which is already globally scaled to deal with over 100 billion messages every day
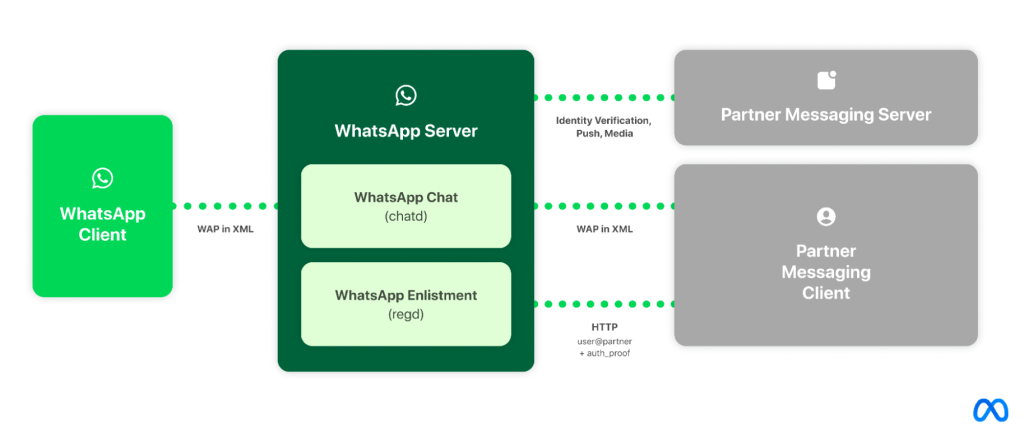
Taking the instance of WhatsApp, third-party purchasers will hook up with WhatsApp servers utilizing our protocol (based mostly on the Extensible Messaging and Presence Protocol – XMPP). The WhatsApp server will interface with a third-party server over HTTP to be able to facilitate quite a lot of issues together with authenticating third-party customers and push notifications.
WhatsApp exposes an Enlistment API that third-party purchasers should execute when opting in to the WhatsApp community. When a third-party person registers on WhatsApp or Messenger, they maintain their current user-visible identifier, and are additionally assigned a novel, WhatsApp-internal identifier that’s used on the infrastructure degree (for protocols, information storage, and many others.)
WhatsApp requires third-party purchasers to supply “proof” of their possession of the third-party user-visible identifier when connecting or enlisting. The proof is constructed by the third-party service cryptographically signing an authentication token. WhatsApp makes use of the usual OpenID protocol (with some minor modifications) alongside a JSON Net Token (JWT Token) to confirm the user-visible identifier by public keys periodically fetched from the third-party server.
WhatsApp makes use of the Noise Protocol Framework to encrypt all information touring between the consumer and the WhatsApp server. As a part of the Noise Protocol, the third-party consumer should carry out a “Noise Handshake” each time the consumer connects to the WhatsApp server. A part of this Handshake is offering a payload to the server which additionally accommodates the JWT Token.
As soon as the consumer has efficiently linked to the WhatsApp server, the consumer should use WhatsApp’s chat protocol to speak with the WhatsApp server. WhatsApp’s chat protocol makes use of optimized XML stanzas to speak with our servers.
As we proceed to debate this structure with third-party suppliers, we predict there’s additionally an strategy to implementing interop the place we might give third-party suppliers the choice so as to add a proxy or an “middleman” between their consumer and the WhatsApp server. A proxy might probably give third-party suppliers extra flexibility and management over what their consumer can obtain from the WhatsApp server and in addition removes the requirement that third-party purchasers should implement WhatsApp’s client-to-server protocol, i.e. preserve their current “chat channel” on their purchasers.
The problem right here is that WhatsApp would not have direct connection to each purchasers and, consequently, would lose connection degree indicators which might be necessary for maintaining customers secure from spam and scams resembling TCP fingerprints. We’d due to this fact anticipate implementing further necessities for third-party suppliers who take up this selection underneath our Reference Supply. This strategy additionally exposes all of the chat metadata to the proxy server, which will increase the probability that this information might be by chance or deliberately leaked.
Clearly explaining how interop works to customers
We consider it’s important that we give customers clear details about how interop works and the way it differs from their chats with different WhatsApp or Messenger customers. This would be the first time that customers have been a part of an interoperable community on our providers, so giving them clear and easy details about what to anticipate can be paramount. For instance, customers must know that our safety and privateness promise, in addition to the function set, gained’t precisely match what we provide in WhatsApp chats.
Privateness and safety is a shared accountability
As is hopefully clear from this submit, preserving privateness and safety in an interoperable system is a shared accountability, and never one thing that Meta is ready to do by itself. We are going to due to this fact must proceed collaborating with third-party suppliers to be able to present the most secure and finest expertise for our customers.












+ There are no comments
Add yours