Trade Server makes use of certificates for:
- Authentication – to confirm {that a} server really is the server that it claims to be.
- Encryption – to forestall theft of or tampering with information in transit by making a safe connection between servers.
To perform these objectives, Trade Server makes use of a number of totally different certificates. On this article, I clarify the several types of certificates, their makes use of, and how one can handle them.
SSL Versus TLS
SSL, which stands for Safe Sockets Layer, is an encryption technique between a server and a shopper developed within the early nineties by Netscape. The never-released SSL model 1.0 was adopted in 1995 by SSL model 2. This model had some weaknesses and was shortly changed by SSL model 3.0 in 1996.
The successor of SSL is TLS, which stands for Transport Layer Safety. TLS model 1 was launched in 1999 and isn’t interoperable with SSL, however TLS 1.0 accommodates a fallback mechanism to make use of SSL model 3.0.
Launched in 2006, TLS 1.1 was an improved model. It was shortly adopted in 2008 by TLS 1.2. Though TLS 1.3 appeared in 2018, TLS 1.2 continues to be very a lot in lively use. Trade 2019 makes use of TLS 1.2 by default and doesn’t but help TLS 1.3. Alternatively, Home windows 2022 helps TLS 1.3. Desk 1 provides an outline of every TLS model and its publication and deprecation 12 months.
| Protocol | Revealed | Standing |
| SSL 1.0 | By no means printed | By no means printed |
| SSL 2.0 | 1995 | Deprecated in 2011 |
| SSL 3.0 | 1996 | Deprecated in 2015 |
| TLS 1.0 | 1999 | Deprecated in 2021 |
| TLS 1.1 | 2006 | Deprecated in 2021 |
| TLS 1.2 | 2008 | In use since 2008 |
| TLS 1.3 | 2018 | In use since 2018 |
Certificates Utilization
Servers use certificates for authentication and encryption. When a shopper needs to arrange a safe connection to a server, the server presents a certificates. Much like the checks carried out at an airport to validate a passport, the FQDN that the shopper makes use of should match the certificates, the certificates should not be expired or revoked, and the issuer of the certificates have to be trusted.
If all checks go, the shopper makes use of the knowledge discovered within the certificates to create a safe connection. If not, what occurs depends upon the circumstances. When utilizing a browser shopper like OWA, the shopper shows a warning message, and you’ll select to proceed to arrange an encrypted connection or shut the browser. If an issue happens with an SMTP connection, the shopper can proceed with a safe connection, however the server just isn’t authenticated. Trying to proceed with an unauthenticated server could current an issue when utilizing area safety or pressured TLS, the place all checks should go. If not, the shopper can not create a connection, and messages can’t be despatched.
Solely the connection is encrypted. The info continues to be despatched unencrypted over the encrypted connection. With eavesdropping, a malicious person can sniff the community site visitors, however not learn the precise information. When a malicious person is able to terminating the connection, he can see the precise contents. This is called a ‘man within the center’ assault. To forestall this, an end-to-end encryption technique can be utilized like S/MIME the place the sending Outlook shopper encrypts the information, and the receiving Outlook shopper decrypts the information.
A certificates accommodates a personal key and a public key. The general public secret is used to encrypt information, the personal secret is used to decrypt the information. The general public secret is all the time accessible, the personal secret is solely accessible on the server that holds the certificates.
To decrypt site visitors from a server, the shopper should get hold of the certificates from the server. The certificates is exchanged utilizing the TLS handshake. That is seen within the SMTP protocol logs as proven in Determine 1.
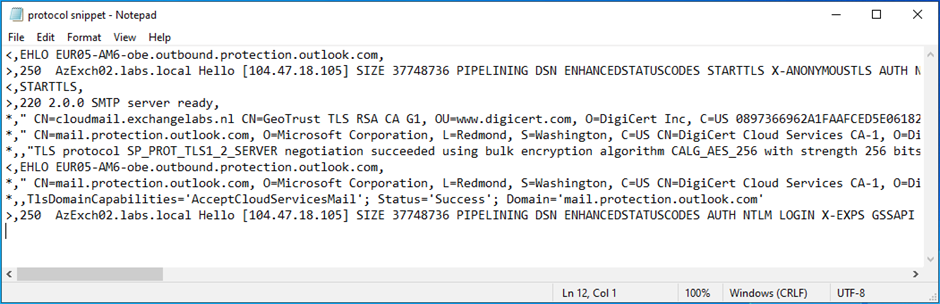
In an Trade hybrid configuration, the certificates on the Trade server have to be a legitimate 3rd celebration certificates. These certificates are issued by a trusted vendor, and all shoppers and servers will robotically belief these distributors and the certificates they situation. If it isn’t a legitimate 3rd celebration certificates, mail movement is not going to work. To work round this, you may go for verifying the IP handle within the Trade Admin Heart as a substitute of the certificates when configuring the Connector.
Trade and Certificates
When an Trade server is put in, it comes with three preconfigured certificates. You may see these certificates utilizing the Get-ExchangeCertificate cmdlet. Right here’s an instance of retrieving Trade certificates info:
Get-ExchangeCertificate -server EXCH01 Thumbprint Companies Topic ---------- -------- ------- A9CF3E1D0DCA5DDA87 ....S.. CN=Microsoft Trade Server Auth Certificates 2259CF7ADEB6D7CDFE IP.WS.. CN=EXCH01 637647FAB458DB7507 ....... CN=WMSvc-SHA2-EXCH01
Observe. The thumbprints have been edited for higher readability.
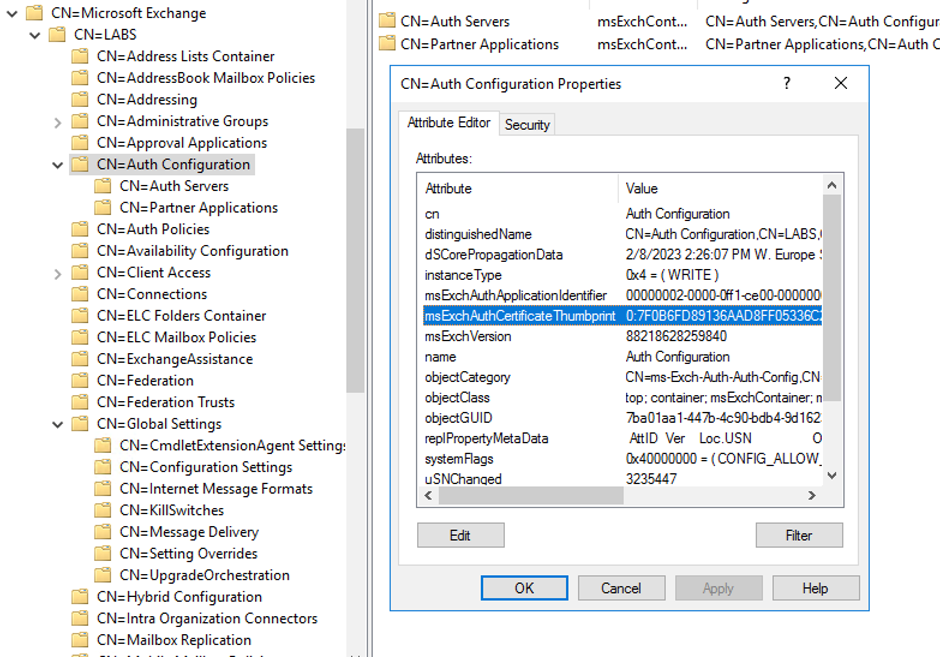
The primary certificates is an authentication certificates used for OAuth authentication in a hybrid surroundings. This certificates is put in on all Trade servers within the group, in addition to on Trade 2016 or Trade 2013 servers when current within the group.
To make this certificates accessible to all Trade servers in a corporation, it’s saved within the configuration partition of Energetic Listing (Determine 2).
The second certificates is the Trade server self-signed server certificates. This certificates is generated throughout set up of the server, and it has a Frequent Identify (CN) with the NetBIOS title of the server. On this instance it’s CN=EXCH01. A second Trade server within the group has a Frequent Identify CN=EXCH02 and so forth.
The self-signed certificates is used to create encrypted TLS connections between Trade servers in the identical group. For the reason that servers are members of the identical Energetic Listing, they robotically belief one another. There’s no want for these servers to make use of certificates to validate connections.
The self-signed certificates may also be used to arrange encrypted TLS connections with exterior SMTP hosts. The certificates is then used for encryption solely for the reason that exterior host can not validate the self-signed certificates. Connections of this kind are known as ‘opportunistic TLS’.
The self-signed certificates can be utilized for connections with shoppers like Outlook on the Net or Outlook, however since this certificates doesn’t comprise the title of the server and it isn’t trusted by the shopper its use generates an error message (Determine 3).
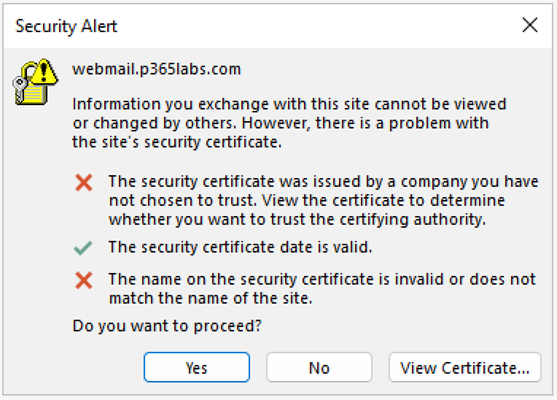
The error message exhibits the FQDN that the shopper needs to entry (on this instance webmail.p365labs.com) and the precise error provoked by the connection. Clearly, the certificates just isn’t trusted and the title on the certificates doesn’t match the title of the positioning. This is sensible for the reason that title on the certificates is CN=EXCH01.
The third certificates with the Frequent Identify CN=WMSvc-SHA2-EXCH01 just isn’t an Trade certificates. That is an IIS self-signed certificates created when the webserver function is put in on the server.
Getting and Utilizing Third-Social gathering Certificates
In a traditional Trade surroundings, you will need to set up a 3rd–celebration certificates. These certificates are trusted by virtually all shoppers. Or higher, the certificates authority that points these certificates is trusted by all shoppers, and subsequently their issued certificates are trusted.
There are a number of distributors promoting these certificates, however I all the time use certificates from Digicert as a result of I do know they work. For an outline of Microsoft certificates necessities, please test the Certificates necessities for hybrid deployments article on the Microsoft web site.
Creating a brand new third-party certificates consists of the next steps:
- Making a certificates request.
- Requesting a certificates from a certificates authority and validating possession of the area.
- Downloading the reply file and finishing the request.
- As a bonus, exporting the certificates for backup functions.
In earlier variations of Trade Server, it was doable to request certificates utilizing the Trade Admin Heart, however with Trade 2019 it is just doable to do that utilizing PowerShell. Right here’s an instance of requesting a brand new certificates with PowerShell:
$RequestData = New-ExchangeCertificate -GenerateRequest -Server EXCH01 -SubjectName "c=NL, S=Noord-Holland, L=Amsterdam, O=Contoso, OU=RND, CN=webmail.p365labs.com" -DomainName webmail.p365labs.com,Autodiscover.p365labs.com -PrivateKeyExportable $true Set-Content material -path C:InstallSSL-Request.req -value $RequestData
These instructions create a textual content file containing the certificates request. Add the contents of the file to the portal of your vendor, validate the possession of the area, and when it was issued, obtain the reply file to your server.
Use the next PowerShell instructions to import the reply file (on the identical server you used to create the request file!):
$Knowledge = [Byte[]]$(Get-Content material -Path "c:installwebmail_p365labs_com.p7b" -Encoding byte -ReadCount 0) Import-ExchangeCertificate -Server EXCH01 -FileData $Knowledge
These instructions import the certificates on the goal Trade server. At this level, the certificates is on the market on the server, nevertheless it doesn’t do something. To allow this certificates for the IIS and SMTP service, use the next PowerShell instructions. The worth of the thumbprint is proven on the console when importing the certificates within the earlier step.
Get-ExchangeCertificate -Server EXCH01 -Thumbprint 603130010099995AD42FBD54856820B9C9AC6BB0 | Allow-ExchangeCertificate -Server EXCH01 -Companies IIS,SMTP
When executing this command, a warning message is proven asking if the default self-signed certificates needs to be overwritten by the brand new certificates.
Overwrite the present default SMTP certificates? Present certificates: '2259CF7ADEB6D7CDFEED739355BE7B32EBBB75FD' (expires 10/4/2028 12:15:41 PM) Change it with certificates: '603130010099995AD42FBD54856820B9C9AC6BB0' (expires 10/4/2024 1:59:59 AM) [Y] Sure [A] Sure to All [N] No [L] No to All [?] Assist (default is "Y"):
I all the time choose ‘No’ since I need the Trade servers to make use of this certificates for server-to-server communication. This certificates can be used for authentication with an Edge Transport server, in order that’s one more reason to maintain the default certificates.
You should utilize the next PowerShell command to export the brand new certificates to a backup file. The instructions take the certificates, ask for a password to set on the backup file after which write the certificates to the backup file.
$Cert = Export-ExchangeCertificate -Thumbprint 603130010099995AD42FBD54856820B9C9AC6BB0 -BinaryEncoded -Password (Get-Credential).password
[System.IO.File]::WriteAllBytes('C:Installwebmail_p365labs_com.pfx', $Cert.FileData)
When a number of Trade servers exist in a corporation, you will need to additionally import the Trade certificates within the different Trade servers. The Import-ExchangeCertificate cmdlet modified in Trade 2019 CU12. In earlier variations, it was doable to make use of the -FileName parameter which accepts UNC filenames. UNC filenames aren’t safe when importing information, so Microsoft eliminated the -FileName parameter from the cmdlet. Beginning with Trade 2019 CU12, you will need to use the -FileData parameter. Right here’s an instance of importing a .PFX file into an Trade server.
Import-ExchangeCertificate -Server EXCH02 -FileData ([System.IO.File]::ReadAllBytes('C:Installwebmail_p365labs_com.pfx')) -Password (Get-Credential).password
Get-ExchangeCertificate -Server EXCH02 -Thumbprint 603130010099995AD42FBD54856820B9C9AC6BB0 | Allow-ExchangeCertificate -Server EXCH02 -Companies IIS,SMTP
This step just isn’t actually wanted, however after putting in a certificates, I all the time recycle the Web Data Server parts utilizing the IISRESET command, and I restart the Microsoft Trade Transport and Microsoft Trade Frontend Transport companies.
Edge Transport Server Certificates
The Edge Transport server function additionally comes with a self-signed certificates. This certificates is used for authentication functions between the Edge Transport server and Trade mailbox servers within the group. Additionally it is used for TLS connections between the Edge Transport server and different mail servers, together with the inner Trade servers.
The method of requesting certificates on the Edge Transport server is equivalent to the method on the inner mailbox servers.
After you create and configure the certificates on the Edge Transport server, you should use the checkTLS device (https://checktls.com) to test your Edge Transport server. After putting in a third-party certificates on the Edge Transport server, you will need to see good outcomes with CheckTLS. Within the following instance, MTA-STS and DANE aren’t configured for this server, however the different assessments are good (Determine 4)
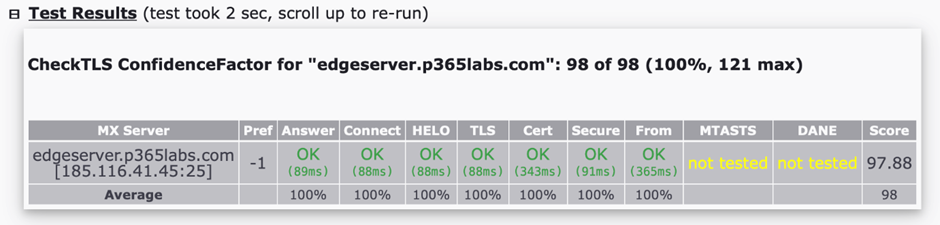
Renewing Certificates
Third-party certificates sometimes have a lifespan of 1 12 months. When this era has virtually expired you will need to request a brand new certificates. Your certificates authority will robotically ship you a notification, sometimes three months prematurely. You should utilize the instructions described above to resume a certificates. As soon as the brand new certificates is put in and configured, you may take away the earlier certificates, nevertheless it does no hurt to go away the expired certificates on the server.
Connecting to Trade On-line
A degree usually forgotten in a hybrid surroundings, however found the onerous manner when cross-premises mail movement halts, is that the certificates should even be configured on the Ship Connector to Trade On-line and the default Obtain Connector.
When the certificates is renewed, replace the Ship Connector out of your Trade server to Trade On-line. Right here’s an instance of updating a Ship Connector with PowerShell:
$TLSCert = Get-ExchangeCertificate -Thumbprint 603130010099995AD42FBD54856820B9C9AC6BB0 $TLSCertName = "<I>$($TLSCert.Issuer)<S>$($TLSCert.Topic)" Set-SendConnector "Outbound to Workplace 365 - <Identifier>" -TlsCertificateName $TLSCertName
Use the next instance to replace the default Obtain Connector on the Trade servers that settle for mail from Trade On-line with the brand new certificates:
Set-ReceiveConnector "EXCH01Default Frontend EXCH01" -TlsCertificateName $TLSCertName
The self-signed certificates and the Trade Auth certificates have a lifespan of 5 years, so these certificates often have an extended lifespan than a mean Trade server.
The OAuth Certificates
The OAuth configuration and its accompanying certificates are used to allow server-to-server authentication utilizing the Open Authorization (OAuth) protocol. This protocol just isn’t solely used for Trade servers, but in addition for Trade On-line, SharePoint On-line, Skype for Enterprise, and Groups integration.
When the primary Trade hybrid configuration is created, an OAuth configuration and an OAuth certificates are created. As talked about within the earlier part, the OAuth certificates has a lifespan of 5 years. That is longer than the conventional lifespan of an Trade server, however not of an Trade hybrid configuration.
Suppose you created an Trade hybrid configuration someplace in July 2019, your OAuth certificates will expire in July 2024. On the time of writing that is solely 5 months away. When the OAuth certificates is about to run out, you will notice warning messages pop up within the Trade On-line Admin Heart.
The OAuth certificates will be renewed manually as documented on this Microsoft article. Microsoft has additionally launched a script known as ‘MonitorExchangeAuthCertificate’ which you’ll obtain on GitHub. The script is way simpler and admin-friendly than the guide process, and it could assist when the OAuth certificates is already expired (which isn’t any enjoyable to cope with utilizing the guide procedures). Utilizing the script is my advice when renewing the OAuth certificates.
Abstract
Trade server makes use of certificates for server authentication and encryption functions. That is for browsers utilizing HTTP(S) and for servers utilizing SMTP. Certificates have to be legitimate, should comprise the proper names, should not be expired or revoked, and ideally issued by a trusted third-party certificates authority.
In Trade 2019, creating, putting in, configuring, and renewing certificates is completed utilizing PowerShell as it’s now not doable to do that within the Trade Admin Heart. When renewing certificates, there’s a gotcha within the hybrid configuration. That is usually forgotten, which ends up in a halted mail movement between Trade 2019 and Trade On-line.













+ There are no comments
Add yours